Whoa!
I’ve been fiddling with Solana wallets for years now, and the browser-extension era feels like a small revolution.
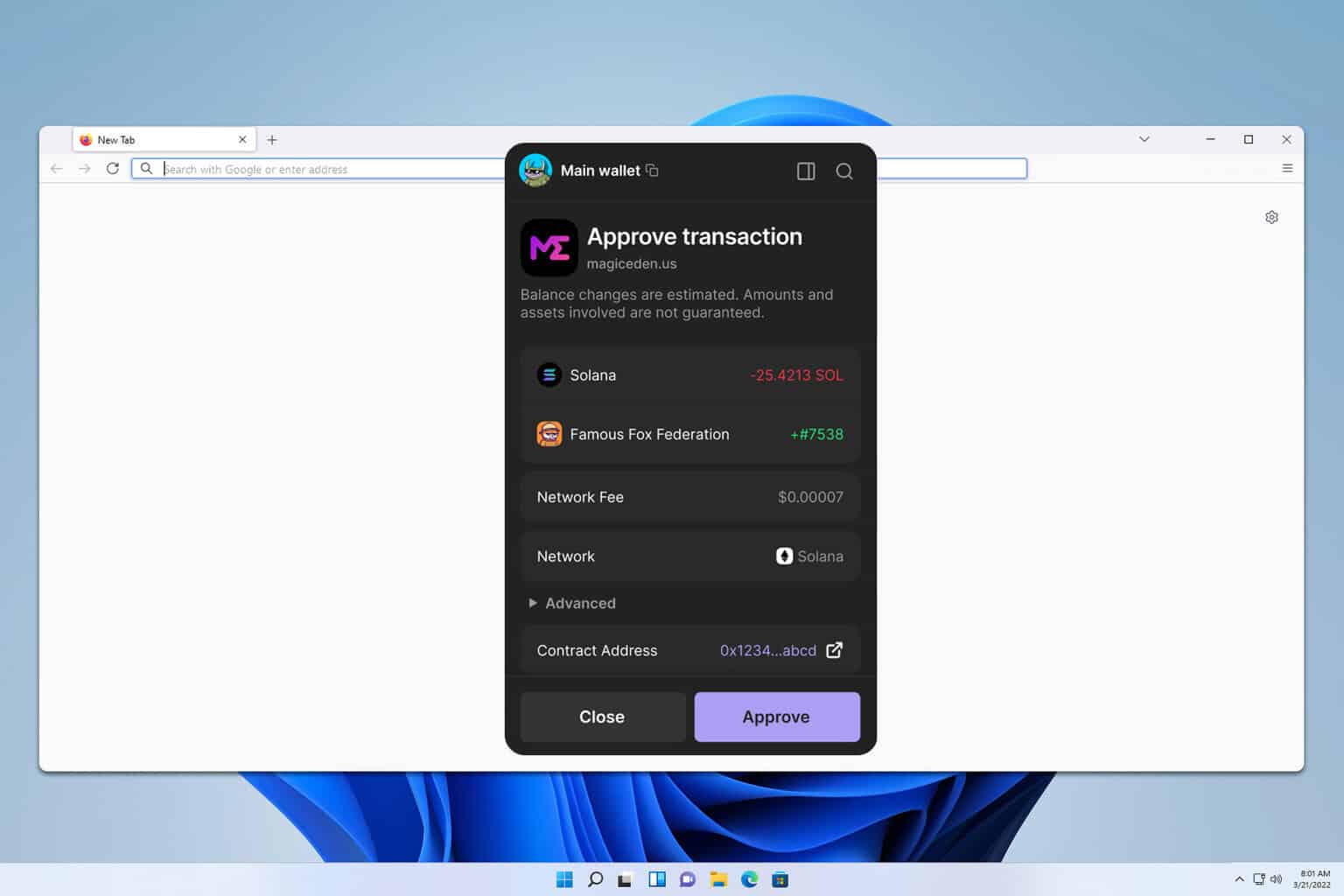
At first glance it’s gloriously simple: sign a transaction, approve a token, flip through NFTs.
But dig a little deeper and you find the usual messy human stuff—permissions, strange pop-ups, and the constant anxiety about a misplaced seed phrase that keeps you up at night.
Here’s the thing: the UX is great, though the security model still asks a lot of you, the human.
Seriously?
Yes—your instinct to be wary is healthy.
Initially I thought browser extensions were the weak link, but then realized the trade-offs are more nuanced: convenience versus custody control versus exposure.
Something felt off about some early extensions I tried; they wanted too many permissions and surfaced cryptic prompts.
Over time I learned to spot the red flags and to trust my gut a bit more before clicking approve.
Hmm… setting one up is usually straightforward.
Open your browser, install the extension, create or import a wallet, and you’re ready to interact with Solana dApps.
If you want a smooth, battle-tested option, try phantom for a clean install flow and sensible UX choices.
My initial impressions were “oh nice” and then “okay, better check the seed backup,” and that pattern repeated across multiple sessions.
Actually, wait—let me rephrase that: install first, then spend a few minutes in settings to lock things down, because that’s where most problems get solved.
Here’s what bugs me about wallet approvals.
Extensions will often prompt you for account access in ways that are technically necessary but morally opaque, and you end up approving things without full context.
On one hand dApps need wallet access to view balances and request signatures; on the other hand, granting access to unvetted sites is asking for trouble.
So I treat each approval like a mini-interview—who are you, why do you want this, and do I trust you enough to proceed?
It’s a small habit that prevents a lot of drama later.
Performance on Solana is delightful compared to many other chains.
Transactions confirm fast, and gas fees (well, fees) are usually low, which makes experimenting with NFTs and micro-transfers less painful.
Still, speed can lull you into risky behavior because confirmations arrive so quickly that you might not parse prompts carefully enough.
My instinct said “go for it” in several cases, and that got me into edge-cases where I had to backtrack and think through how to revoke allowances or recover from a careless click.
So fast networks are great, but they demand a slightly higher awareness level—we move fast, and sometimes too fast.
Wallet design matters more than people realize.
A small UX nudge—like clearer wording around “sign message” versus “approve transaction”—reduces mistakes dramatically.
I like extensions that separate view-only permissions from signing capabilities, because the separation forces you to confront the risk before it happens.
I’m biased, but a clean, minimalist interface usually correlates with a team that thinks about security and not just growth.
Still, even beautiful UIs can hide dangerous defaults, so check the defaults—always check them.
NFTs are a whole other vibe.
Minting feels like grabbing a concert ticket that might be worth something or might become a digital paperweight.
When you connect your wallet to an NFT minting site, you’re not just handing over a signature—you might be authorizing approvals that persist until revoked.
That persistence is the subtle risk where many folks get burned, because a permission issued during a hype window can be exploited weeks later.
So I make it a habit to periodically review active approvals and revoke any that look unfamiliar or unnecessary.
On the technical side, extensions use injected providers to let dApps talk to your wallet.
This is powerful, but it also means any website loaded in your browser gets to ask for access, and some sites are more trustworthy than others.
A good pattern is to use multiple browser profiles: one for general browsing, one for DeFi and NFT interaction, and another purely for admin tasks like checking balances.
It feels a bit overkill, but isolation reduces the blast radius if a malicious site sneaks in.
Oh, and keep your browser up to date—browser vulnerabilities still get exploited and that can bypass extension-level protections.
Recovery planning is very very important.
Write down your seed phrase on paper and store it in a safe place, not on a cloud note with your name attached, please.
If you lose access, recovery is the only route back, and the methods you choose shape how resilient you are to loss or theft.
I once used a simple fireproof box and it gave me so much peace of mind that I still recommend it to friends and family.
That said, hardware wallets add another layer of safety if you’re storing significant value—consider them if you’re serious.
Troubleshooting common extension woes is mostly about clearing state.
If a dApp can’t see your account or transactions fail, try reconnecting, restarting the browser, or re-importing the wallet from your seed into a fresh profile (careful!).
Network mismatches sometimes cause odd errors, especially with testnets and devnets, and it’s easy to overlook which cluster you’re on.
Pro tip: if you suspect a malicious prompt, don’t just dismiss it—take screenshots and document what happened before making changes, because patterns repeat and information helps.
These small rituals help you feel more in control when things go sideways.
Privacy is often misunderstood in the web3 world.
Your extension doesn’t just hold keys; it also exposes addresses which are public and traceable, and your interaction graph with dApps leaks behavioral signals.
Use different addresses for different activities if you want plausible deniability or better compartmentalization, though that brings bookkeeping overhead.
If you connect to analytics-heavy platforms, understand that metadata can be used to deanonymize patterns over time.
I won’t pretend I’m fully anonymous—I’m not—but I’m mindful, and that’s half the battle.
Mobile versus browser extension is a frequent debate.
Mobile wallets let you sign on the go and often feel more integrated with device biometrics, while browser extensions shine for heavy-duty dApp interactions and NFTs.
I use both, but I keep the lion’s share of funds in cold storage when I expect to hold long-term.
For day-to-day fiddling and testing new drops, an extension sandboxed in a separate profile is my go-to.
Balance convenience with caution; you’ll sleep better that way.
Okay, so where does that leave us?
I’m cautiously optimistic about Solana’s wallet ecosystem because the tooling is improving and teams care about UX, but complacency is the enemy.
My instinct said earlier that browser extensions were risky, yet systematic hardening and a few good habits made them my primary interface for years.
On one hand they’re wonderful—fast confirmations and crisp NFT flows—though actually, on the other hand, they demand respect and constant attention to permissions.
In short: use them, enjoy them, but treat your seed phrase like it’s the key to your house, because well… it is.
Quick FAQ
How do I revoke a malicious approval?
Check your wallet’s settings for “connected sites” or “approvals” and revoke any unknown entries; if the extension lacks a revoke UI, use a reputable on-chain tool that lists token approvals and revoke via a safe interface—don’t sign anything unless you’re sure.
Is a browser extension safe for NFTs?
Short answer: yes for casual collecting, but for high-value items use extra precautions like hardware wallets or isolated profiles; I’m not 100% sure about every edge-case, but separation and regular approval audits reduce risk greatly.

